Are you concerned about the security of confidential information within your company? Optimal Security is On IT’s managed security offering and provides total protection for your network, devices and data.
From firewall optimization to 24/7 threat detection and response, our team of experts will work with you to develop a customized security plan, supervise its implementation and handle its maintenance.
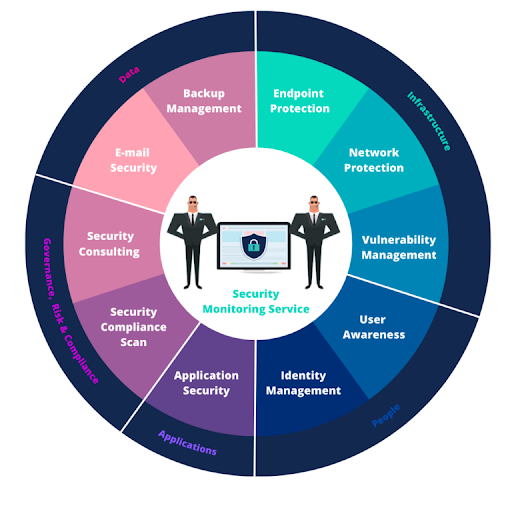
Optimal Security provides an arsenal of security measures:
"Security information/event monitoring" (SIEM) combined with a "24/7 security operating center" (SOC) are the essential building blocks of any security strategy and includes three key components:
By endpoints we mean not only your server infrastructure - on premise, hybrid or in the cloud - but also devices such as computers, cell phones, tablets, IoT devices, which end users use to access and thus access the network. Securing these devices is the first line of defense for your company's network security.
Thanks to a number of applications installed on all devices, attacks are prevented, detected and resolved.
"Network Protection" or Network Security is a particularly broad term. With Optimal Security, the focus is primarily on incoming and outgoing traffic and providing secure accesses for your remote and/or home-based employees. On the other hand, it also prevents access to dangerous domains and protects users from inventive cyber-attacks. Reporting and analysis tools provide detailed insight into Internet usage and the dangers potentially associated with it.
Firewall Protection is the solution to strengthen the security of your network perimeter and protect your business from external threats and unwanted access. With this service, you get a powerful, simple way to ensure that all firewalls always meet the latest security standards and consistently perform to the highest baselines.
With Firewall Protection, you choose a proactive approach. We continuously monitor and manage your firewall configurations so that systems are always optimally protected. No hassles, no worries - you can count on maximum security with minimum effort.
This solution is designed to keep your network secure while maximizing compliance with any applicable guidelines and regulations. This allows you to fully focus on your core business, while we ensure that your digital environment remains reliable and protected.
"Identity Management" is an essential building block of a secure IT environment. By extending the standard password policy to include conditional accesses and enforcing multi-factor authentication, you can be more confident that the logged-in user's identity is real.
Take it a step further by having risky and impossible logins automatically blocked and reporting your users' login behavior.
Hacks and breaches are a common phenomenon. Unfortunately, in more than 70% of cases, human interaction is at the root. End users are not always aware of current threats and their key role in them. This is why we are bringing "User Awareness" more to the forefront.
Thanks to training and information sessions, users stay better informed of the possible dangers. Your IT teams are not forgotten either: with customized sessions and training sessions, they are updated on an ongoing basis.
Vulnerability Management is a continuous, proactive and automated process that screens computer systems networks and applications for vulnerabilities that increase the risks of successful cyber-attacks. 'Agentless' your network is periodically scanned through robotic processes, identifying and reporting any vulnerabilities.
Our solution acts as an ongoing, proactive security audit that operates unobtrusively in the background. This ensures early identification of potential weaknesses and security breaches. Based on clear, well-organized reports, we then prioritize and implement targeted improvement actions. In this way, you are always one step ahead of cyber attacks and your organization remains optimally protected.
The term "Application Security" or application security covers all measures, techniques and processes to be applied to protect applications from threats, vulnerabilities and attacks. The goal is to ensure that applications operate reliably and securely, and the risk of data breaches or disclosure is sensitively reduced. Among other things, we look at user authentication and authorization, data encryption, input validation, and monitoring and logging of application usage.
Backup management ensures not only that sufficient and complete backups are taken, but also that obsolete backups are monitored, tested and deleted. Only in this way can you be sure of reliable data stored in a professional manner.
It is an ongoing process and addresses the frequency, timing, content and scope of backups. Moreover, it also provides a distinction between critical and less critical data and, based on that distinction, will take appropriate measures to make its recovery proportional in the event of a disaster.
Email Security protects email accounts and email messages from unauthorized access, loss and modification of content. Indeed, the risks today are manifold and include malware, spam and phishing attacks.
E-mail is a common target because it is relatively easy to access and is also very susceptible to human error. Accidentally clicking on a wrong link can already cause a major security problem.
Increasingly, a connection is being made between security and compliance. On the one hand, between security as a set of systems and controls, on the other by external agencies and the standards imposed. Just think of NIS2, SOX, HIPAA, and ISO. Or the regulations related to GDPR.
Many companies and industries are required, by law or as a best practice, to comply with such standards when conducting their operations. It is therefore interesting to automate auditing and reporting on this, and this is increasingly part of a holistic security strategy.
To know the state of your IT environment in terms of security, a Security Consultant from On IT can audit your network, identify its strengths and weaknesses and deliver a global report. This report reflects the current situation and is accompanied by a list of recommendations to achieve the desired security status.
This is especially relevant when your IT environment has grown over the years, where technological developments and the operational needs of your business have led to a complex situation.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.